At Facets, we understand the intricacies involved with complex engineering setups. As organizations scale and multiple teams work simultaneously, ensuring seamless operations becomes paramount. Today, we're introducing our latest feature: Guardrail policies, a solution designed to streamline policy management for your entire infrastructure using the power of Open Policy Agent (OPA) integration.
Let’s dive into the details.
What are Guardrails?
In the context of Platform Engineering and DevOps, Guardrails are like predefined rules or policies that guide developers and teams toward adhering to certain standards or best practices during the software development lifecycle. This ensures that everyone on a development team moves in the same direction toward achieving the common goals of a project.
The Platform or DevOps team sets guardrails and creates an environment where developers can make decisions independently, maintain collaboration, enable faster decisions, and mitigate risks associated with software development. Instead of everyone provisioning infrastructure in opinionated ways or your operations team running around doing it, guardrails provide regulated autonomy.
Why do you need guardrails?
When you adopt Platform Engineering principles, it becomes crucial that you have a well-defined framework of policies that ensure operational efficiency and compliance. The Guardrails feature can potentially help you in the following ways:
Consistent and standardized Infrastructure:
With multiple developers working with different end goals, there’s an increased risk of conflicting resource details or incorrect configurations, leading to increased manual intervention and configuration management. Guardrails promote consistency and standardization across your infrastructure by employing best practices. It helps in reducing errors and misconfigurations and easing the troubleshooting process thereby saving time and enhancing output quality.
Cost Management
Inefficient resource utilization and unnecessary expenses arise from overprovisioning, resulting in resource wastage and additional costs. Guardrails help teams provision resources optimally by setting limits on cloud resource allocations to reduce the risk of cost overruns.
Security, Compliance, and Auditability
In the face of tightening regulatory and compliance requisites, guardrails serve as a beacon of compliance assurance. Moreover, they mitigate the risks associated with security infringements by ensuring databases are configured accurately and cloud storage buckets are not publicly accessible without proper authorization.
Enhancing efficiency and collaboration
Guardrails boost operational efficiency and facilitate swift decision-making as teams have a coherent understanding of what’s permissible and what’s not. They also foster a collaborative culture by aligning all members of the development team toward common goals.
Facets’ Guardrail Policies
In Facets' Guardrail policies can be used by the Ops or Platform teams to create, manage, and enforce policies seamlessly. Leveraging the versatility and domain-agnostic nature of Open Policy Agent, this integration ensures policy decision-making is decoupled from enforcement, resulting in a more efficient and streamlined workflow.
Why Open Policy Agent?
The choice of OPA was strategic. We’ve seen that a lot of policy enforcement is done manually - in wikis or docs, giving rise to tribal knowledge. Moreover, the ecosystem of policy enforcement is fragmented. To solve for this, we wanted to take a unified policy enforcement approach across the entire technology stack. OPA's ability to handle the entire policy ecosystem seamlessly, coupled with its capacity to integrate with various tech tools, made it the ideal solution for our platform.
How it works in Facets
With the integration of OPA, Facets enables users to manage and enforce policies through Facets UI.
Policy Creation and Management
OPA allows you to define and update policies independently of your application code. You can express rules and policies using Rego, a language used to write logic-based policies. This separation of concerns makes it easier to manage and evolve policies.
In Facets, you can define policies based on blueprints, environments, resource types, and resource names. By applying policies on resource types, or environment level, it becomes easier to enforce and manage policies for multiple resources.
Users can easily create, view, edit, and manage policies from a centralized location. In the upcoming release, we’ll also be providing users with the option of cloning, enabling, and disabling the policies.
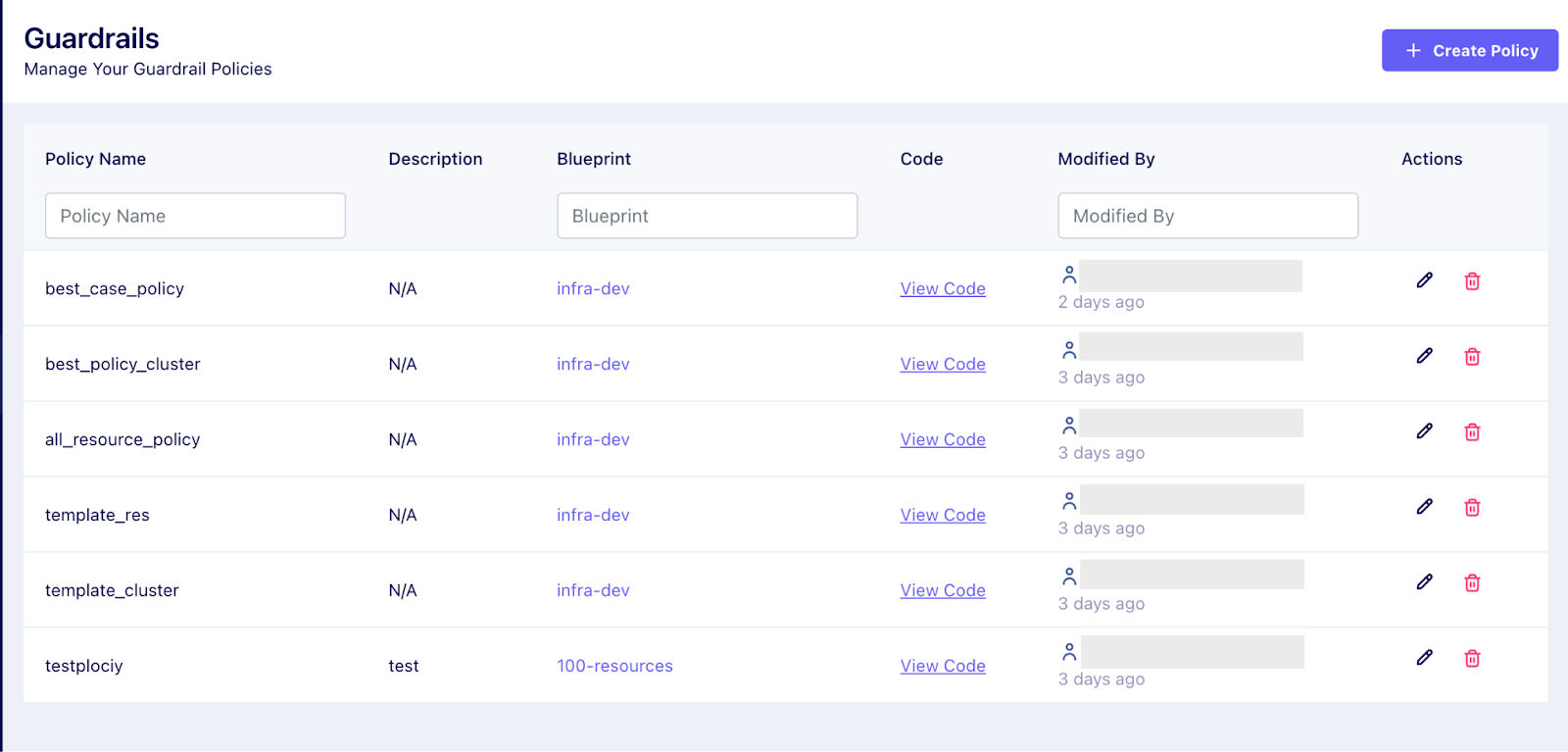
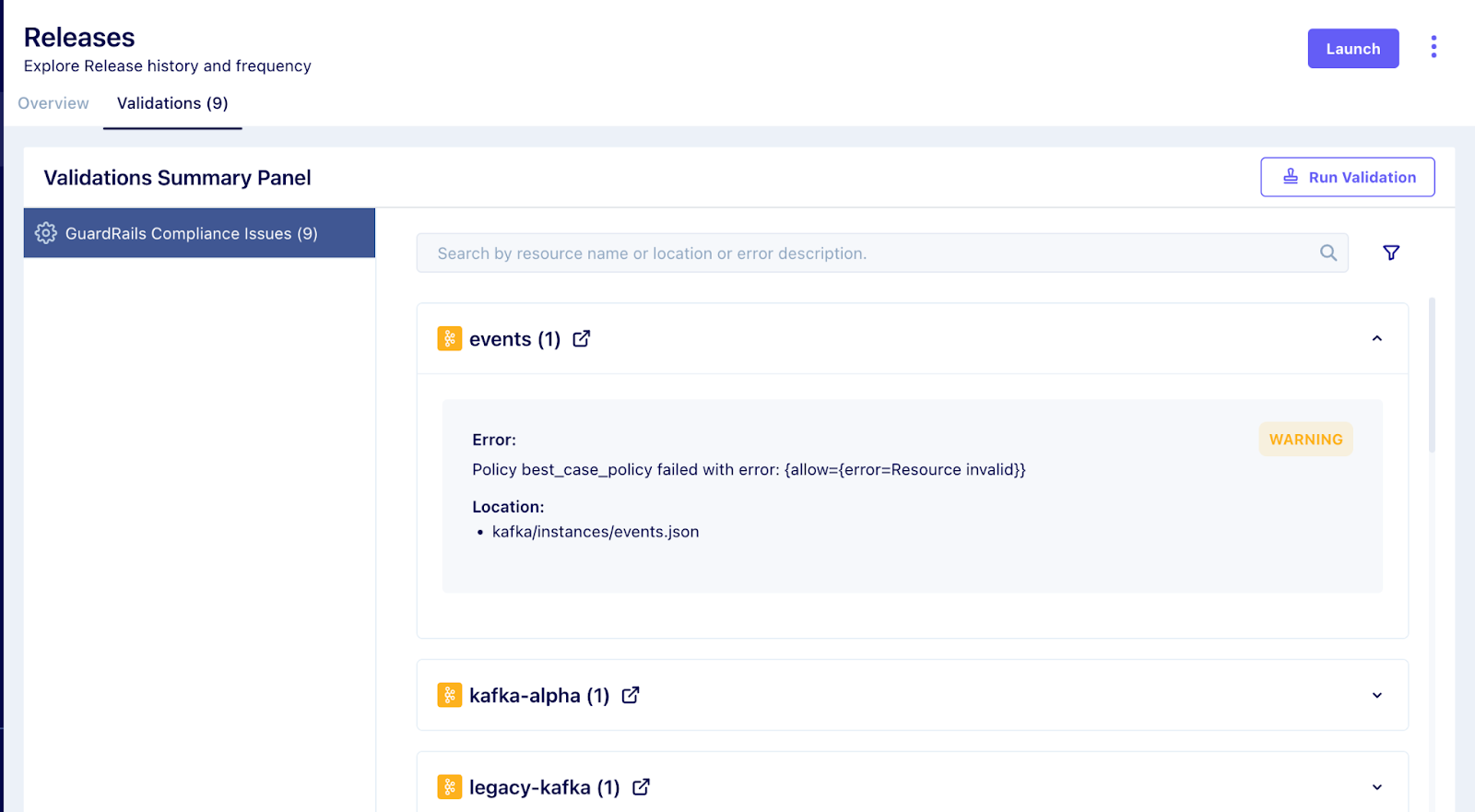
Policy Application and Violations
In Facets, policies are enforceable based on selected criteria, such as specific blueprints, environments, resource types, and resource names.
To make policy enforcement easier, users will receive feedback on policy violations, including details of the violation and suggestions for resolution. We’ve also added severity tags to policies by flagging warnings and errors. Users can also block releases if errors are critical.
Use-cases
Here are some use cases where setting guardrails can help in standardization, security, and operational efficiency:
Resource Provisioning Limits: You can set guardrails to limit the maximum resources that can be provisioned for specific services or applications. For example, you can restrict teams from requesting more than 3 cores for applications in any environment.
Security Compliance Enforcement: It ensures that all systems have the latest security patches installed, strong password policies, and firewall rules. For example, you can set guardrails to ensure S3 buckets are not public, and EC2 instances of certain types are not allowed.
Network Access Control: You can implement strict rules for network traffic, such as restricting access to specific IP addresses or network segments, or employing VPNs for secure remote access.
Data Backup and Retention Policies: You can define policies for data retention periods and backup frequency to prevent data loss in the event of hardware failures, natural disasters, or cyber-attacks.
Compliance Monitoring for Cloud Services: This includes monitoring data encryption, access control, and data residency requirements to maintain compliance with regulations such as GDPR or HIPAA.
Resource Tagging Policies: Implementing guardrails for resource tagging ensures that all resources are appropriately labeled with relevant metadata.
Conclusion
With the introduction of Guardrail Policies powered by Open Policy Agent integration, Facets aims to streamline policy management for all infrastructure needs. With this, users can enable real-time policy evaluation for evolving environments. Moreover, Facets provides a centralized location to manage policies so everyone has complete visibility of rules. This ensures that resources are optimally provisioned, and have security best practices baked in. Get started with guardrails and improve Developer and Ops experience.