Configuration and secret management is crucial for deploying applications securely and reliably. Traditional methods often involve manual updates, scattered secrets, and environment-specific files. These practices can lead to increased overhead, elevated vulnerabilities, and hinder scalability.
As we delve deeper into environment management strategies across various companies, these challenges consistently emerge as recurring pain points, hindering efficient software delivery and secure operations—particularly as teams, projects, or environments scale.
This part of our series explores the common challenges the developers and DevOps engineers face with traditional configuration and secrets management.
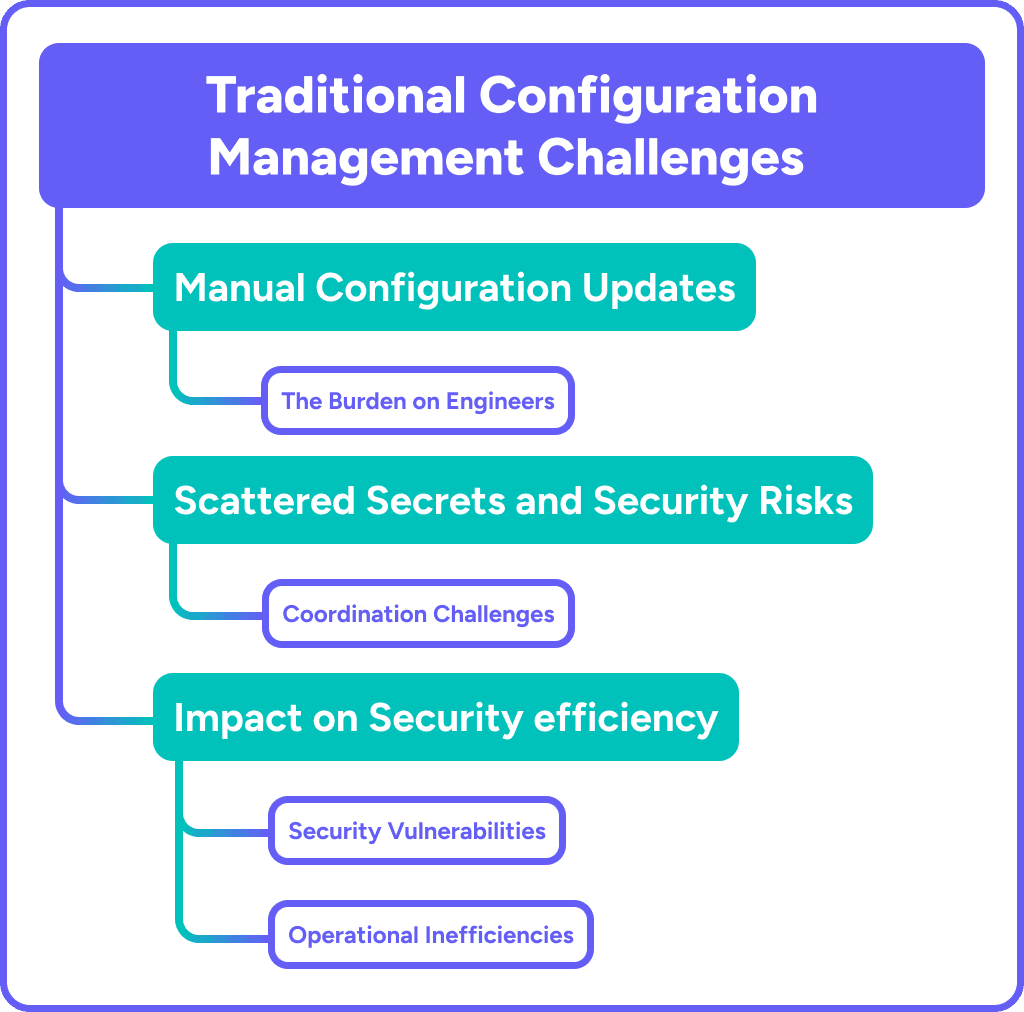
Manual Configuration Updates and Environment- Specific Files
The Burden on Engineers
Managing configurations manually across multiple environments is time-consuming and error-prone. Each environment—development, staging, production—typically requires its own set of configuration files. This approach leads to:
Increased Maintenance Effort: Updating configurations in multiple places whenever a change is needed requires higher effort and diligence
Risk of Inconsistencies: Manual edits can introduce discrepancies between environments, causing unexpected behavior.
Delayed Deployments: Time spent coordinating and verifying configurations slows down the release cycle.
Example Scenario
Suppose you have an application that requires specific database connection strings and API keys for each environment. Managing these settings manually means any update requires editing multiple configuration files, increasing the chance of errors.
Scattered Secrets and Security Risks
Challenges with Secret Management
Even when using secrets management tools, traditional practices often involve applications accessing secrets directly. This introduces several issues:
Insecure Access Patterns: Applications fetching secrets directly can expose them if not handled properly.
Coordination Overhead: Ensuring that the secret identifiers in the code match the actual secrets stored is error-prone.
Complex Secret Management: Rotating and updating secrets across environments becomes an administrative burden.
Coordination Challenges
Aligning the secrets used in code with those stored in secret management systems can be difficult:
Manual Synchronisation: Developers need to update code references when secrets change or new ones are added.
Environment Discrepancies: Different environments may have different secrets, requiring careful coordination.
Limited Visibility: Tracking which secrets are used and where can be challenging without a centralised system.
Impact on Security and Efficiency
Security Vulnerabilities
Exposure of Sensitive Data: Vulnerabilities in the application can potentially expose secrets.
Inconsistent Access Controls: Direct access may bypass centralized policies.
Audit Difficulties: Monitoring which applications access specific secrets becomes more complex.
Hard-Coded Credentials: Embedding secrets in configuration files or code increases the risk of exposure.
Inadequate Rotation Practices: Rotating secrets regularly is challenging without automated processes.
Operational Inefficiencies
Increased Workload: Engineers spend significant time managing secrets instead of focusing on development.
Error-Prone Processes: Manual creation and distribution of secrets can lead to misconfigurations.
Scalability Issues: As the number of applications and environments grows, managing secrets becomes more complex.
Delayed Response to Threats: Manual processes slow down the ability to respond to new requirements or security threats.
Resource Drain: Time spent on manual configuration and secret management distracts developers from development efforts.
Conclusion
In summary, traditional configuration and secret management pose the following challenges:
High Maintenance Overhead: Manual updates and environment-specific files increase workload and risk of errors.
Security Risks: Scattered secrets and direct application access expose systems to vulnerabilities.
Coordination Complexity: Synchronising secrets between code and secret stores across environments is labor-intensive.
In the next part of this series, we'll explore how adopting Infrastructure as Code (IaC) can address these challenges by automating configurations and securely managing secrets per environment.